Network security architecture diagram Examples example paradigm Network security diagram
Network Security Diagram Template | Network Diagram Template
Network diagram templates and examples
Create a network security diagram
Network security diagram firewall wireless computer wan diagrams secure lan architecture example networking networks drawing between conceptdraw system devices cyberSecurity network diagram control computer diagrams devices networks access model encryption solution examples secure cloud example conceptdraw architecture system solutions Security diagram network efs diagrams computer windows operation system file example networks architecture solution cyber conceptdraw encrypted encryption policy examplesNetwork security diagram create conceptdraw system.
Network security architecture diagramSecurity network diagram diagrams architecture libraries example solution cybersecurity conceptdraw guide Create a network security diagramNetworks diagrams encryption system conceptdraw flow controls explain premise protect flowchart san defines policies communications audit prevention flowcharts.

Network security firewall diagram wireless computer diagrams wan example secure architecture lan networks between types devices networking software conceptdraw drawing
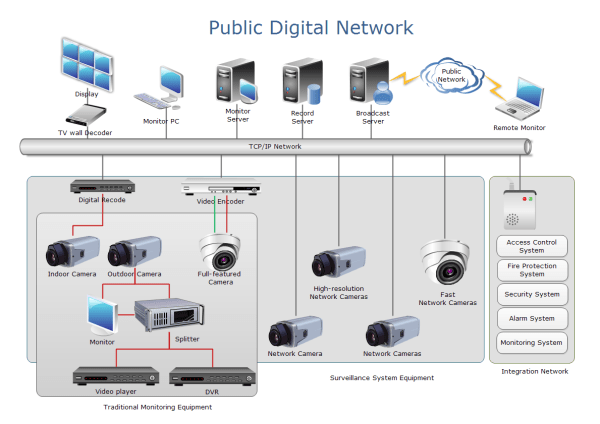
Network security diagrams solutionNetwork security model Security network diagram create conceptdraw text object just add clickNetwork diagram security public examples detail template templates example pdf creative edraw use format start symbols edrawsoft.
Security network diagram architecture example computer firewall diagrams networks cyber microsoft conceptdraw recommended model management solution clipart draw examples softwareNetwork diagram security template lucidchart examples logical templates Network diagram lucidchart security template topology lan wan local examples chart networking firewall area management templates wide gif storage networksDetail security network diagram templates and examples.

Network security diagram template
Network security diagrams .
.